
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) Introduction In the era of digital transformation, organizations are moving to the cloud at an unprecedented pace. While the
🔥Premium Monthly Plan – Only $11.99!🔥Hurry! This exclusive deal won’t last long. 👉 Subscribe Now!

Cloud Security Posture Management (CSPM) Introduction In the era of digital transformation, organizations are moving to the cloud at an unprecedented pace. While the

How to Strengthen Security Using CIS Controls and Posture Analysis Introduction In the fast-paced and ever-evolving world of cybersecurity, defending digital infrastructure goes far

How to Prepare for the AWS Data Engineer Exam Introduction With the world becoming increasingly data-driven, organizations are depending on cloud-based systems to store, process,
Table of Contents
The world is currently dominated by modern, cutting-edge technology. Information security is one of the most crucial elements of today’s advanced technology. Hackers target the increasing amount of data with various malicious purposes, but the company has certified ethical hackers who can stop these data breaches. This article covers detailed knowledge of Certified Ethical Hackers (CEH).
The Certified Ethical Hacker (CEH) offers a thorough comprehension of ethical hacking phases, diverse attack vectors, and protective countermeasures. To effectively set up your security infrastructure and fight against assaults, it will show you how hackers think and act. The CEH course equips students with knowledge of system flaws and vulnerabilities and teaches them how to protect their businesses and strengthen their security procedures to lower the risk of a malicious attack.
The complete cybersecurity curriculum for producing knowledgeable and proficient ethical hackers is Certified Ethical Hacker v12. Since CEH v12 is now the entire cybersecurity curriculum, it stands apart from other industry credentials. It offers practical treatment of the five stages of ethical hacking in the technologies used today. Any firm must be aware of these five steps of ethical hacking; the more you know about a hacker’s capabilities, the better you can prevent attacks.
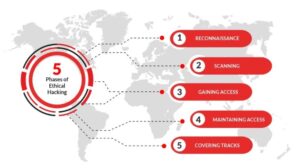
In order to analyze the security posture of a target system, a certified ethical hacker uses the same knowledge and tools as a competent hacker, but lawfully and legitimately. They are skilled professionals who understand and know how to hunt for holes and vulnerabilities in target systems (s). From a vendor-neutral standpoint, the CEH certificate accredits individuals in the unique network security discipline of ethical hacking.
The CEH credential’s objectives are to:
The CEH certification teaches users how to exploit the knowledge and resources used by malicious attackers to identify vulnerabilities in the target organization’s systems. For 20 years, many organizations have ranked CEH as the top ethical hacking certification in the world. On September 7, 2022, EC-Council released the latest CEH program, the new CEH v12.
The revised learning framework contains the most comprehensive, in-depth, hands-on lab and practice range experience available in the market and a comprehensive training program to prepare you for the certification exam. A successful career in cybersecurity is possible with the CEH v12 certification.
The Learn, Certify, Engage, and Compete learning paradigm was created by CEH v12 and follows a 4-step technique.
With practical labs that offer thorough training, this learning strategy enables participants passing the CEH v12 program to have an in-depth learning experience that will prepare them for the certification exam.
Around the new learning framework, CEH v12 integrates training, practical learning labs, certification exams, practice in cyberspaces, and cyber contests. The Learn, Certify, Engage, and Compete phases make up this learning system.
The CEH v12 training program’s 20 courses cover various technologies, tactics, and strategies, giving aspiring ethical hackers the knowledge they need to succeed.
Step-by-step labs in a virtualized environment support every approach, goal, and tool taught in training.
One of the most respected credentials in the world and a crucial gauge of ethical hacking and security testing concepts is the Certified Ethical Hacker title.
Industry experts examine each qualified participant to ensure their certification maps adhere to the most current industry standards. This exam is regularly subjected to psychometric testing to guarantee a fair and accurate assessment of the candidate’s expertise in ethical hacking.
Participants in the four phases of CEH v12 must exercise critical thought and use their newly learned information and abilities. In the EC-new Council’s Cyber Range, participants will display and capture several flags at each level, showcasing the real-world application of skills and abilities in a results-neutral setting.
The competitive phase, brand-new in CEH v12, offers monthly competitions in Capture the Flag, OT, IoT, SCADA, and CEH Web Applications that expose you to various cutting-edge platforms and technologies.
The CEH v12 test has 125 multiple-choice questions and lasts 4 hours. The CEH v12 prepares you to comprehend the most recent commercial hacking tools, methods, methodologies, and ways of getting around security controls used by real-world hackers. This knowledge-based exam will test the understanding of identifying system vulnerabilities, attack vectors, attack detection, attack prevention, processes, techniques, and other topics.
The six-hour CEH v12 practical exam is complex. It requires you to demonstrate proficiency in ethical hacking techniques like port scanning, vulnerability detection, and attacks on a system (like DDoS, DoS, session hijacking, web server and web application attacks, SQL injection, wireless threats, etc.).
CEH specialists are in demand due to the increased impact of hacker threats and attacks. Contrarily, there are still fewer available positions, meaning there are more job chances for those interested.
The goal of CEH v12 is to prepare applicants for certification and competition by teaching them the whole body of information and abilities through a brand-new learning process. As a result, they become a critical certified part of the cybersecurity community.
With a focus on emerging technology challenges, such as containerization, Serverless computing, Operational Technology (OT), Cyber Kill Chain, and machine learning, including the full malware analysis process, CEH v12 covers new modules for the security against emerging attack vectors and modern exploit technologies. Our CEH booklet provides a thorough grasp of proactive vulnerability assessment and security gap in a real-world setting.
| Exam Questions | MCQs |
| Number of Questions | 125 |
| Time to Complete | 240 minutes |
| Exam Fee | 850 USD |
| Certification Validity | 3 years |
| Passing Score | 70% |
| Domain | Sub-Domain | No of Questions | Weightage |
| Information Security and Ethical Hacking Overview | Introduction to Ethical Hacking | 8 | 6% |
| Reconnaissance Techniques | Footprinting and Reconnaissance | 10 | 21% |
| Scanning Networks | 10 | ||
| Enumeration | 6 | ||
| Cloud Computing Cryptography | Vulnerability Analysis | 9 | 17% |
| System Hacking | 6 | ||
| Malware Threats | 6 | ||
| Network and Perimeter Hacking | Sniffing | 3 | 14% |
| Social Engineering | 5 | ||
| Denial-of-Service | 2 | ||
| Session Hijacking | 3 | ||
| Web Application Hacking | Hacking Web Servers | 8 | 16% |
| Hacking Web Applications | 8 | ||
| SQL Injections | 4 | ||
| Wireless Network Hacking | Hacking Wireless Networks | 8 | 6% |
| Mobile Platform, IoT, and OT Hacking | Hacking Mobile Platforms | 4 | 8% |
| IoT and OT Hacking | 6 | ||
| Cloud Computing | Cloud Computing | 7 | 6% |
| Cryptography | Cryptography | 7 | 6% |
The Certified Ethical Hacker certification program has different versions; the most recent is CEH (v12), while the oldest is CEH (v11). While both editions cover a wide range of ethical hacking-related subjects, CEH (v12) has updates and new information that reflect the most recent developments and methods.
Since it ultimately depends on a person’s needs and objectives, it is difficult to determine whether a version of the Certified Ethical Hacker (CEH) certification program is “better.” The most recent and thorough version of the certification program is usually regarded as CEH (v12).
Updates and new material reflecting the most recent ethical hacking trends and methods are included in CEH (v12), along with information on emerging technologies, including cloud computing, the Internet of Things (IoT), and Artificial Intelligence (AI). Additionally, a module on Security Orchestration, Automation, and Response (SOAR), a relatively recent idea in cybersecurity, is included.
The certification program’s older iteration, CEH (v11), may have only some upgrades and content. Although it is still a respected and valuable certification program, professionals who want to stay up-to-date in their industry might prefer the more thorough and current training offered by CEH v12.
The CEH v12 is a unique and specialized training course that will provide you with the necessary ethical hacking knowledge. Keep up with the most in-demand abilities essential to succeed in the cybersecurity industry.
© 2025 All rights reserved | Privacy Policy | Terms and Conditions | Sitemap | Cookie Policy




