
Zero Trust vs. SASE: Everything You Need to Know
Zero Trust vs. SASE: Everything You Need to Know Introduction As the cyber world continues to change, companies need to look beyond conventional security
🔥Premium Monthly Plan – Only $11.99!🔥Hurry! This exclusive deal won’t last long. 👉 Subscribe Now!

Zero Trust vs. SASE: Everything You Need to Know Introduction As the cyber world continues to change, companies need to look beyond conventional security

Cloud Security Posture Management (CSPM) Introduction In the era of digital transformation, organizations are moving to the cloud at an unprecedented pace. While the

How to Strengthen Security Using CIS Controls and Posture Analysis Introduction In the fast-paced and ever-evolving world of cybersecurity, defending digital infrastructure goes far
Table of Contents
Cybersecurity is an ever-growing concern in the modern world, and organizations need all the help they can get to ensure their data remains safe.
Azure Sentinel is a cloud-native SIEM solution that integrates with existing solutions from Microsoft, such as Office 365 and Windows Defender Advanced Threat Protection (ATP). It also integrates with third-party solutions from other vendors, such as Symantec, Palo Alto Networks, and Splunk. This allows you to create a unified security platform that can detect threats quickly and easily.
Azure Sentinel uses machine learning to analyze large volumes of data from various sources, including your on-premises networks, public clouds, endpoints, applications, servers, and even social media sites. This allows it to detect anomalies in behavior that could indicate malicious activity or cyberattacks. It can also identify suspicious network traffic and alert you in real-time if suspicious activity is detected. This article covers detailed knowledge of Azure Sentinel.
The following are the four key phases or regions of Azure Sentinel:
It can gather information on all users, gadgets, programs, and infrastructure locally and across various cloud settings. For Microsoft solutions, numerous connectors offer real-time integration. It also has integrated connections for goods and services from third parties (non-Microsoft Solutions). The necessary data sources can also be connected to it using Common Event Format (CEF), Syslog, or REST-API, among other methods.
The use of analytics and threat intelligence obtained directly from Microsoft can identify threats and reduce false positives. Azure Analytics greatly aids the security team’s ability to link warnings to occurrences. To build threat detection rules and automate threat responses, it offers built-in templates right out of the box.
It can look into and track questionable activity anywhere. It aids in noise reduction and security threat detection using the MITRE framework. You can use artificial intelligence to spot risks across the protected assets before an alert is triggered to catch suspicious activity.
Built-in orchestration incidents may be handled swiftly and flexibly, and automating routine and common tasks is simple. The playbooks can be used to provide streamlined security orchestration.
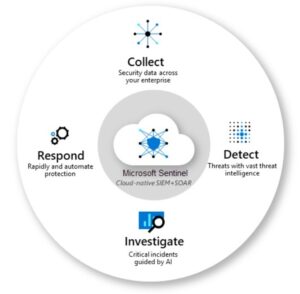
Azure Sentinel collects data from various sources, such as logs, events, alerts, network traffic, endpoints, and other sources. This data is then ingested into the Azure platform and analyzed using machine learning algorithms to detect potential threats. Once a threat is detected, the system can trigger an alert or automated response based on predefined criteria. This allows for quick detection of malicious activities so that appropriate steps can be taken before any damage has been done. Azure Sentinel also offers rich visualizations of your organization’s security posture so that you can stay up-to-date with the latest threats.
In addition to detecting threats in real time, Azure Sentinel also offers powerful insights into your organization’s security posture over time by providing access to historical data so that you can see trends or changes in behavior over time.
Let’s examine some of Azure Sentinel’s benefits:
Azure Sentinel provides real-time insights and analytics through its extensive library of built-in data connectors that can be used to collect and analyze data from various sources, including Office 365, Active Directory, Azure AD, Azure Security Center, etc. Additionally, it can integrate with third-party solutions such as Splunk or IBM QRadar so that you can leverage their insights as well. This allows you to quickly identify suspicious activities and take action to prevent potential attacks before they happen.
Azure Sentinel offers flexible deployment options so you can choose what works best for your organization. You can deploy it in a hybrid environment that includes both on-premises resources and cloud services, or you can opt for an entirely cloud-based approach if that better suits your needs. Furthermore, its scalability means it can easily accommodate any size organization without requiring additional hardware or software investments.
Azure Sentinel uses advanced machine learning algorithms to detect anomalies in your system that could indicate malicious activity or suspicious behavior. It then automatically generates alerts so you can investigate further and take appropriate action if required. This helps save time by eliminating manual reviews and reduces the risk of false positives by providing more accurate results faster than traditional methods of threat detection & response.
Azure Sentinel has a data storage limitation of 500 GB per workspace. It is important to remember that this limitation applies across all collected logs for each workspace. This means that your overall storage limit will also be reduced if you have multiple workspaces. Additionally, if you are collecting logs from multiple sources, your 500 GB limit could be reached quickly depending on the volume of logs generated.
Azure Sentinel also has a limitation when it comes to analytics capabilities. While the solution does offer some basic analytics tools, such as dashboards and reports, these tools are limited in scope. They must provide a different level of detailed analysis than more advanced analytics solutions such as Splunk or Tableau. Additionally, Azure Sentinel’s analytics capabilities are limited by its data storage capacity; if your data exceeds 500GB, then any additional analysis will need to be done outside Azure Sentinel.
Finally, a performance limitation associated with Azure Sentinel may affect your ability to use the software effectively in certain situations. The performance of the software depends heavily on factors such as network latency and server processing power; if either of these factors is lacking, then your experience with Azure Sentinel may need to be better. Additionally, since Azure Sentinel runs in the cloud, any outages or downtime experienced by Microsoft can directly impact the availability of your security operations platform.
The future of Azure Sentinel looks promising as it continues to gain popularity among organizations that want to improve their security posture and stay ahead of emerging security threats. The following are a few potential future developments for Azure Sentinel:
Azure Sentinel is a powerful tool for protecting your business against cybersecurity threats. Integrating with existing Microsoft solutions and third-party products from other vendors provides an enhanced level of visibility into your network while minimizing response times when malicious activity is detected.
© 2025 All rights reserved | Privacy Policy | Terms and Conditions | Sitemap | Cookie Policy




