
How to Apply Cybersecurity in Fintech for User Protection
Introduction As fintech evolves, it brings innovative financial solutions that enhance user convenience, such as mobile banking, digital lending, and secure payments. However, as financial
Exclusive Discount Offer: Unlock 3-Months of IPSpecialist’s Premium Plan for Just $59.99 $15.99! Save $44 Today! Subscribe Now!

Introduction As fintech evolves, it brings innovative financial solutions that enhance user convenience, such as mobile banking, digital lending, and secure payments. However, as financial

Introduction In the realm of cloud computing, Amazon Web Services (AWS) offers a variety of managed database options that help organizations scale, secure, and optimize

Introduction In the ever-evolving landscape of cybersecurity, zero-day attacks pose a significant threat to businesses and individuals alike. A zero-day attack exploits a software vulnerability
Table of Contents
The majority of people envision a cyberattack as a one-time transfer. A hacker gains access to the system, downloads essential documents and information, and then exits. However, this is only sometimes the case.
Even if the initial attack is unsuccessful, not every cyber threat ends there. A cyberattack on a well-organized system can take a long time and money to complete. They are typically organized by cybercriminal groups known as APT groups. This article covers detailed knowledge of Advanced Persistent Threat (APT).
Check out our courses now to start your career in Networking and Cybersecurity.
An Advanced Persistent Threat (APT) is a coordinated cyberattack carried out by several knowledgeable, experienced threat actors. APTs do not include a “hit and run” strategy. Attackers take a long time to prepare their campaign and execute it against strategic targets meticulously.
APTs are multi-stage compound attacks that use a range of attack methods. Zero-day exploits and malware, specialized credential theft, and lateral movement tools are just a few of the frequently used attack vectors that were first released as a part of an APT operation. APT campaigns frequently use several attack vectors and access points.
You must identify an APT’s characteristics to stop, find, and stop it. The majority of APTs use the same basic life cycle to infiltrate a network, get access, and complete the objective of the attack, which is typically data theft using network extraction.
Advanced persistent threats frequently use social engineering strategies to obtain access during the first phase. Phishing emails that selectively target high-level personnel, such as senior executives or technology leaders, frequently using data collected from other team members who have already been infiltrated, are one sign of an APT. “Spear-phishing” refers to email attacks that target particular people.
Attackers introduce malware into an organization’s network after gaining initial access to proceed to the second step, expansion. They move laterally to map the network and collect login information, including account names and passwords, to gain access to vital corporate data.
Cybercriminals often keep stolen data until enough data has been gathered in a protected location within the network to prepare for the third phase. They then stealthily extract it, or “exfiltrate,” it. To occupy network staff and divert the security team’s attention while the data is being exfiltrated, they might employ strategies like a denial-of-service (DoS) attack. The network may still be infected, ready for the burglars to strike again at any moment.
APT Groups employ techniques that differ from those used by other hackers who your systems are designed to detect. Here are some advanced persistent threat characteristics to be on the lookout for.
An increase in elevated logins could be the first sign of a sophisticated, persistent threat. By utilizing accounts with greater access and permissions, APTs can compromise an entire environment in hours.
As these hackers use higher-level accounts, you can check in with the various departments to see when their executives are accessing the network. When an outside user accesses the information, it should be obvious.
APT threats have also been known to cause unexpected data flows, such as an email being intercepted by another computer. Some cloud email systems track the location from which messages are accessed, but not all of them.
You may also encounter spear-phishing emails sent to upper-management employees who may unintentionally grant a hacker access.
Threat actors also install backdoor Trojan programs to ensure they can re-enter the system if one of their entry points is compromised.
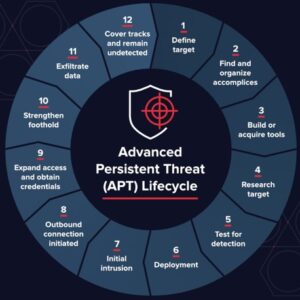
APT is a type of attack that should be on the radar of all businesses. Small and medium-sized businesses should take into account this type of attack.
APT attackers increasingly use smaller companies that are part of their ultimate target’s supply chain to gain access to large organizations. They use such companies as stepping stones, as they are typically less well-defended.
Effective APT detection and protection necessitate a multifaceted approach from network administrators, security providers, and individual users.
Monitoring ingress and egress traffic are regarded as the best practice for preventing the installation of backdoors and preventing the extraction of stolen data. Inspecting traffic within the network perimeter can also help security personnel detect unusual behavior that may indicate malicious activity.
A Web Application Firewall (WAF) deployed at the network’s edge filters traffic to web application servers, protecting one of the most vulnerable attack surfaces. A WAF, among other things, can help weed out application layer attacks like RFI and SQL injection, commonly used during the APT infiltration phase.
The other side of this equation is internal traffic monitoring services, such as network firewalls. They can provide a granular view of how users interact within the network while also assisting in detecting internal traffic anomalies (e.g., irregular logins or substantial data transfers). The latter could indicate an APT attack is underway.
Employees are typically the most significant and vulnerable soft spot in the security perimeter for perpetrators. Intruders frequently view network users as an easy way to infiltrate the defenses while expanding their hold within the security perimeter.
In this case, likely targets fall into one of three categories:
Whitelisting is a method of controlling domains accessed from the network and applications that the users can install. Another effective method for lowering APT attacks’ success rate is reducing the available attack surfaces.
This security measure, however, could be better, as even the most trusted domains can be compromised. It is also common for malicious files to disguise themselves as legitimate software.
Several intelligence and cybersecurity products are available to help firms better defend against APT strikes. Here are some of the most effective strategies to use:
Sensor Coverage – To prevent blind spots that could turn into safe havens for cyber threats, organizations must implement capabilities that give their defenders complete visibility across their environment.
Technical Intelligence – It utilizes technical intelligence, such as indications of compromise (IOCs), and incorporates them into security information and event management (SIEM) for data enrichment. This makes it possible to undertake event correlation with more intelligence, potentially emphasizing network events that might not have been noticed otherwise.
Service Provider – It is essential to collaborate with a best-in-class cybersecurity company. Organizations may need help responding to a sophisticated cyber threat if the unimaginable occurs.
Web Application Firewall – A web application firewall, often known as a WAF, is a security tool created to safeguard enterprises at the application level by filtering, observing, and analyzing HTTP and HTTPS traffic between the web application and the internet.
Threat Intelligence – It helps with malware family tracking, campaign tracking, and threat actor profiling. Threat intelligence is crucial in today’s world because it is increasingly more critical to comprehend the context of an attack than simply to know that it occurred.
Threat Hunting – Many firms will discover the need for controlled, human-based threat hunting available around the clock to go along with their existing cybersecurity technology.
The Advanced Persistent Threat (APT) severely threatens cybersecurity. Its unique high unpredictability, deep concealment, and serious harmfulness pose unprecedented challenges to traditional network monitoring technology in the context of massive and complicated network traffic.
© 2024 All rights reserved | Privacy Policy | Terms and Conditions | Sitemap | Cookie Policy




