
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) Introduction In the era of digital transformation, organizations are moving to the cloud at an unprecedented pace. While the
🔥Premium Monthly Plan – Only $11.99!🔥Hurry! This exclusive deal won’t last long. 👉 Subscribe Now!

Cloud Security Posture Management (CSPM) Introduction In the era of digital transformation, organizations are moving to the cloud at an unprecedented pace. While the

How to Strengthen Security Using CIS Controls and Posture Analysis Introduction In the fast-paced and ever-evolving world of cybersecurity, defending digital infrastructure goes far

How to Prepare for the AWS Data Engineer Exam Introduction With the world becoming increasingly data-driven, organizations are depending on cloud-based systems to store, process,
Table of Contents
Penetration testing, often known as pen testing, evaluates the security of computer systems, networks, or online applications by simulating an attack by a hostile actor. Penetration testing aims to identify vulnerabilities, weaknesses, and potential security risks in the target system or application that attackers can exploit.
Penetration testing can be done manually, through automated tools, or a combination. The process involves several phases: surveillance, vulnerability scanning, exploitation, and post-exploitation. The goal is to identify and exploit vulnerabilities in a controlled environment to determine the potential impact of an attack and provide recommendations for remediation.
The results of a penetration test are usually documented in a report that includes a summary of the testing methodology, the vulnerabilities found, the severity of the vulnerabilities, and recommendations for remediation. Organizations of all sizes utilize penetration testing to find and reduce security threats since it is a crucial part of a comprehensive security program. This article covers detailed knowledge of Pentester and how it can prevent data breaches.
Pentesters are usually accountable for adhering to the hiring agency’s or organization’s testing guidelines. Full-time pentesters typically begin with an objective before deciding which tools and techniques will best enable them to achieve it. Pentesters create paperwork outlining the findings of their tests after finishing them to aid in implementing security changes.
Pentesters require strong vocal and written communication skills in addition to technical expertise. To develop solutions based on the findings of the tests, pentesters frequently need to work with the IT staff. Pentesters must keep up with the most recent developments in the cybersecurity sector due to the kinds of attacks that are occurring in the real world and the tools that cybercriminals use.
The following are the different types of penetration testing:
Network Penetration Testing: This type of testing involves evaluating the security of network infrastructure, such as firewalls, routers, switches, and servers.
Web Application Penetration Testing: This type of testing focuses on identifying vulnerabilities in web applications, such as online shopping sites, banking sites, and social media sites.
Mobile Application Penetration Testing: This type of testing involves evaluating the security of mobile applications on different platforms such as Android, iOS, and Windows Mobile.
Wireless Penetration Testing: This testing involves evaluating the security of wireless networks, such as Wi-Fi, Bluetooth, and ZigBee networks.
Social Engineering Penetration Testing: This type of testing involves evaluating employees’ security awareness by simulating social engineering attacks such as phishing emails, pretexting, and baiting.
Physical Penetration Testing: This testing involves attempting to gain unauthorized access to physical infrastructure, such as data centers, offices, and warehouses, to evaluate its security.
Red Team Penetration Testing: This type of testing involves simulating a real-world attack by an external threat actor to identify vulnerabilities and test the organization’s security defenses.
Each type of penetration testing serves a different purpose and helps organizations identify and remediate security vulnerabilities in their systems, networks, and applications.
Penetration testing is essential for several reasons:
Identifying Security Vulnerabilities: The use of penetration testing can aid in locating vulnerabilities that may have gone unnoticed over the course of development or ignored by routine security audits. This allows organizations to identify and remediate security issues before attackers can exploit them.
Simulating Real-World Attacks: Penetration testing simulates a real-world attack scenario, allowing organizations to understand how attackers might attempt to exploit vulnerabilities and how they could be prevented.
Meeting Compliance Requirements: Many industry regulations and standards require regular security assessments and penetration testing to ensure compliance. Organizations that fail to meet these requirements can face legal and financial consequences.
Reducing the Risk of a Security Breach: By finding and resolving vulnerabilities, penetration testing can help lower the chance of a security breach and the related expenses of data loss, system unavailability, and reputational harm.
Improving Overall Security Posture: Penetration testing can help businesses enhance their overall security posture by finding places where security controls can be reinforced, offering insight into potential attack routes, and indicating areas where security training and awareness may be needed.
Overall, penetration testing is a crucial part of a thorough security program and should be carried out regularly to help detect and address security issues.
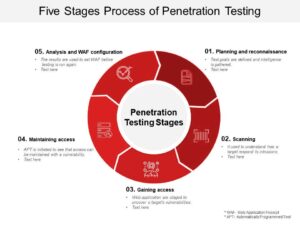
Pen testing, or penetration testing, simulates an assault on a computer system or network to find security holes that an attacker might exploit. The stages of penetration testing typically include:
Planning and Surveillance: The first stage of pen testing involves understanding the target system or network and identifying potential vulnerabilities. This includes gathering information about the target, such as IP addresses, domain names, and network topology.
Scanning: In this stage, the pen tester uses tools to scan the target system or network for vulnerabilities. This can include port scanning, vulnerability scanning, and web application scanning.
Gaining Access: Once vulnerabilities have been identified, the pen tester attempts to exploit them to gain access to the target system or network. This may involve using tools such as password-cracking software, social engineering techniques, or exploiting vulnerabilities in software.
Maintaining Access: Once access has been gained, the pen tester will attempt to keep access to the target system or network. This may involve setting up backdoors or planting malware to enable future access.
Analysis and WAF Configurations: In this final stage, the pen tester will attempt to cover their tracks to avoid detection. This may involve deleting log files, modifying system configurations, or obscuring their presence on the target system or network.
Security employees examine this data to assist in configuring an enterprise’s WAF settings and other application security tools to fix vulnerabilities and defend against upcoming attacks.
Organizations are working to proactively spot network risk areas because data breach costs are at an all-time high. Pen testing, also known as vulnerability testing, is increasingly popular. Businesses must identify their risk areas before hackers do to defend themselves. By eliminating or mitigating vulnerabilities, organizations can reduce their attack risk.
The average cost of data theft in 2022, as reported in IBM’s Cost of a Data Breach study, is $4.35 million, an increase of 12.7% from 2020. Breach situations are increasingly becoming a matter of “when,” not “if,” for many companies. Only 17% of the organizations taking part in the survey claimed this was their first data breach, while 83% reported multiple breaches.
Due to this, many businesses are using pen testing to raise their total security. While Pentesters cannot prevent data breaches independently, their work is essential to an organization’s security strategy. The following are some ways that Pentesters can help prevent data breaches:
Identifying Vulnerabilities: Pentesters are skilled at identifying vulnerabilities in systems, networks, and applications that attackers could exploit. By finding these vulnerabilities before attackers do, organizations can fix them before they can be used and prevent a data breach.
Testing Security Controls: Pentesters can help organizations determine if their security controls prevent or mitigate attacks effectively. They can test security controls like firewalls, intrusion detection systems, and access controls to ensure they work as intended.
Providing Recommendations: Pentesters can suggest improving an organization’s security posture after conducting a penetration test. This can include changes to policies, procedures, or technical controls.
Raising Awareness: Pentesters can help raise awareness among employees about the importance of security and how to identify potential threats. This can include training on recognizing phishing emails, using strong passwords, and other security best practices.
Overall, while Pentesters cannot prevent data breaches independently, their work is essential to a larger security strategy that can help organizations prevent and protect their sensitive information.
Although penetration testing is costly and time-consuming, your organization must have security protocols that allow it to identify vulnerabilities before bad actors do. The insights you get from a pentest can help you mitigate security risks and avoid future data breaches and losses.
© 2025 All rights reserved | Privacy Policy | Terms and Conditions | Sitemap | Cookie Policy




