
How to Harden Your Infrastructure Using CIS Benchmarks
How to Harden Your Infrastructure Using CIS Benchmarks Introduction As more organizations go faster with their digital transformation, the security and resilience of IT infrastructure
Limited-Time Offer! Get an exclusive 40% OFF on IPSpecialist Premium Monthly & Annual Plans. Use Promo Code: UPSKILLNOW at checkout.

How to Harden Your Infrastructure Using CIS Benchmarks Introduction As more organizations go faster with their digital transformation, the security and resilience of IT infrastructure

Azure Certifications – Validate Your Azure Cloud Skills Introduction Cloud computing has transformed the business landscape, providing scalability, flexibility, and affordability in a way

Top Cyber Security Trends: What Every Organization Must Know Introduction In an era marked by digital transformation, remote workforces, and rapidly evolving threat landscapes,
Table of Contents
Microsoft 365 Defender is an enterprise defense solution that provides unified protection against sophisticated threats by providing threat protection and detection across endpoints, email, and applications. The suite includes four primary products from which to pick. This article covers detailed knowledge of Microsoft 365 Defender.
To assist security professionals in focusing on what is essential by ensuring that the complete extent of the attack, impacted assets, and automated remedial steps are grouped and surfaced promptly.
To help stop the advancement of an attack, critical threat information is transmitted in real-time among Microsoft 365 Defender products.
If a malicious file is found on an endpoint protected by Defender for Endpoint, Defender for Office 365 will be instructed to scan and remove the file from all email communications. The complete Microsoft 365 security suite will block the file on sight.
Microsoft 365 Defender remediates affected assets using AI-powered automatic actions and playbooks. Microsoft 365 Defender uses the suite’s automatic remediation capabilities to guarantee that any impacted assets associated with an event are automatically remediated where possible.
By generating custom queries on the raw data collected by the various protection technologies, security teams can leverage their unique organizational knowledge to seek signs of compromise. Microsoft 365 Defender gives you query-based access to the last 30 days of raw signal and alert data from endpoints and Defender for Office 365 data.
Microsoft 365 Defender automatically collects, correlates, and analyses threat, alert, and signal data from the Microsoft 365 ecosystem, including email, endpoints, identities, and applications. To halt attacks and undertake cleanup, the solution employs Artificial Intelligence (AI) and automation.
The diagram below depicts the high-level architecture for some of the most prominent Microsoft 365 Defender connectors and components.
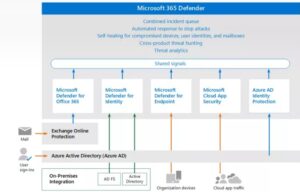
Microsoft 365 Defender collects information from all Defender components. The approach distributes aggregated signals to the complete Defender ecosystem, which leverages this data to provide the following services:
Microsoft 365 Defender safeguards against vulnerabilities offered by links (URLs), collaboration tools, and email communications. It captures and distributes signals from these activities to the Microsoft 365 Defender ecosystem. The system connects with Exchange Online Protection (EOP) to safeguard all incoming emails and attachments.
Microsoft Defender for Identity assists in the protection of hybrid identity environments. The service collects and processes signals from Active AD FS and on-premises Active AD DS servers. It can assist in preventing actors from moving laterally by utilizing compromised accounts. You can also use Azure AD Identity Protection to assess sign-in threats and set up conditional access controls.
Microsoft Defender for Cloud Apps safeguards data as it travels between cloud apps and the environment. Defender for Cloud Apps gathers signals from sanctioned and unapproved cloud apps to secure data between the corporate environment and the apps.
The diagram below depicts an attack attempt that was foiled by the Microsoft 365 Defender suite:
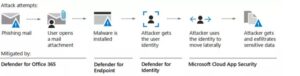
The diagram depicts the typical processes of phishing schemes. It usually begins with a phishing email arriving in the inbox of a specific user, usually an organization employee. Unaware of the dangerous content, the user opens the email attachment and unintentionally installs malicious software (malware) on the device.
Once deployed, the virus seeks to carry out the tasks for which it was designed, such as stealing confidential data. Defenders for Office 365, on the other hand, can minimize this attack at multiple stages by utilizing its array of defenders. The following are the primary capabilities used by Defender for Office 365 to protect against phishing schemes:
This Microsoft Defender for Office 365 function is designed to detect phishing emails. It employs mail flow controls to ensure that a phishing email does not reach the inbox, hence preventing the phishing attempt from succeeding.
This Defender for Office 365 tool assesses the safety of attachments. If the feature determines that the attachment is malicious, it prevents the user from acting on the message. Policies, on the other hand, may block mail from reaching the inbox.
This EDR solution handles network-connected devices. It can detect and prevent network and device vulnerabilities.
This system is capable of detecting sudden account changes as well as high-risk lateral movement. It also reports easily exploitable identity vulnerabilities.
This technology detects unusual behavior and reports it to your security staff. It can detect abnormal activity such as credential access, impossible travel, and unusual downloads and file shares. It can also detect unusual mail forwarding activity.
Microsoft 365 Defender services protect:
Defender for Endpoint is a single platform that delivers proactive endpoint security, post-breach detection, automated investigation and response, and incident management.
Microsoft Defender Vulnerability Management provides continuous asset visibility, intelligent risk-based assessments, and built-in remediation tools to assist your security and information technology teams in prioritizing and address significant vulnerabilities and misconfigurations across your organization.
Defender for Office 365 protects your organization from dangerous attacks via email, links (URLs), and collaboration tools.
Microsoft Defender for Identity is a cloud-based security service that uses the signals from your on-premises Active Directory to identify, detect, and analyze advanced threats, compromised identities, and harmful insider acts directed at your organization. Azure AD Identity Protection protects your users by leveraging Microsoft’s experience in organizations with Azure AD, the consumer space with Microsoft Accounts, and gaming with Xbox.
There are two pricing tiers for Microsoft Defender for Office 365, ranging from $2 to $5.
Security professionals can easily interpret threat signals received by each of these products using the integrated Microsoft 365 Defender solution to determine the scope and impact of the threat.
© 2025 All rights reserved | Privacy Policy | Terms and Conditions | Sitemap | Cookie Policy




